What seemed like a massive cyberattack on the Tax Agency has taken an unexpected turn. After days of investigations, the AEAT has confirmed that There was no breach in their systems or compromised taxpayer data .
The real objective was a Private agency in Malaga , which handles tax information for small businesses and individuals. The famous figure of " $38 million " that the Trinity hackers mentioned comes from internal documents of this agency, not the Treasury.
This case leaves a clear lesson: the Cybersecurity it does not end in public systems . Private companies that handle sensitive information must also strengthen their defenses to avoid becoming the weak link. Collaboration between the two sectors will be key to facing future risks, especially with the imminent arrival of Verifactu , the real-time billing system. In this article, we look at what happened, who's behind it, and the essential lessons for businesses in the new digital environment.
Who is Trinity
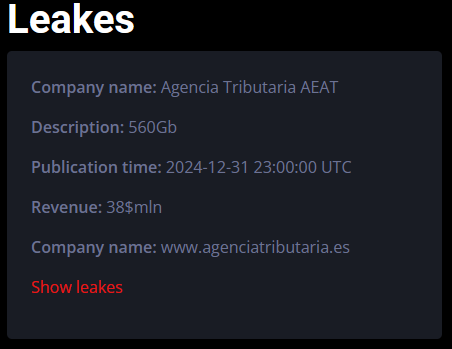
Trinity is a hacker group specializing in the use of double-extortion ransomware. This method involves extracting sensitive data from organizations and then encrypting their systems, demanding a ransom to prevent the information from being leaked. In this case, they managed to take 690GB of data from the Tax Agency, which includes tax and personal information of thousands of taxpayers and public employees. And they are asking for a ransom of 38 million dollars not to publish them.
How: The attack according to the new research
After days of uncertainty, the alleged hack of the Tax Agency turned out to be a threat aimed at a private agency, not the AEAT. Initially, the Trinity group claimed to have stolen 560 GB of tax and personal data, demanding a ransom of 38 million dollars. However, subsequent investigations revealed that the compromised data belongs to an independent tax consultancy. The figure of "38 million" was mistakenly interpreted as a ransom demand, when in fact it appears to correspond to internal documents of the affected company.
How to: Potential vulnerabilities
Although the Tax Agency was not hacked, the case leaves important lessons. Affected companies are often victims of insecure remote access, outdated software, or phishing strategies, such as fraudulent emails that trick employees into stealing credentials. The rise of remote work has increased these risks, as many organizations still do not strengthen their systems against growing threats.
When and where: the chronology that confused everyone
It all started on November 29, when Trinity published on the dark web an alleged proof of the hack. Although they never contacted the Tax Agency, they claimed to have critical tax data. The announcement generated a media stir, but days later, the AEAT denied the attack after analyzing its systems and confirming that no suspicious activity had been detected on its servers. The real victim was an agency in Malaga whose data was compromised and used to support the claims of the hacker group.
This outcome shows that, although there was no breach in the Tax Agency, attacks on collaborating companies can have a similar impact. The lesson is clear: cybersecurity must be strengthened throughout the data management chain.

The Goal Behind the Trinity Threat: What Really Happened
Trinity claimed to have stolen 560 GB of tax data from the Tax Agency (AEAT), demanding a ransom of $38 million by December 31, 2024. However, after several days of investigations, it was confirmed that the AEAT systems were not breached. The alleged "rescue" seems to have been based on internal financial documents of a private agency in Malaga, whose data was compromised and used as a basis for media extortion.
Double extortion: a dangerous strategy
Although the attack on the AEAT turned out to be false, Trinity's modus operandi remains an example of "double extortion": first, they steal information and then threaten to disclose it if they do not receive a payment. Their strategy plays with the urgency of the victims, especially when it comes to tax or personal data that could damage the reputation of public institutions or private companies.
These types of threats seek more than just money. They try to generate distrust in public management and create an image crisis. If the leak had been real, it would have seriously impacted thousands of taxpayers and employees, even affecting the tax system in the process of implementing Verifactu, the real-time invoicing system that will come into force in 2024.
Preventive measures and exposed vulnerabilities
Although there was no hacking in the Tax Agency, the reputational damage and media confusion were evident. The AEAT temporarily suspended teleworking and reinforced its security measures. This case shows that cybersecurity does not depend only on one's own systems, but also on third parties that manage sensitive data.
The lesson is clear: in a digitized and highly interconnected world, any weak link can be used as an entry point. The real attack occurs not only on servers, but also on public trust and the perception of institutional security.

A Warning on the Eve of Verifactu: Beyond the Trinity Attack
The Trinity case, although it did not affect the Tax Agency, is a clear reminder of the risks faced by companies and public entities in an increasingly complex digital environment. This is especially relevant in the face of the imminent arrival of Verifactu , the real-time invoicing system that will directly connect companies with the Treasury from 2024.
Verifactu will force all invoices to be transmitted and recorded automatically and constantly. While it promises greater fiscal transparency, it also expands the attack surface for Cybercriminals , which could try to compromise companies connected to the tax network. This makes each company a potential vulnerability.
How companies should prepare
Faced with this scenario, companies must act now to strengthen their cybersecurity:
- Shield remote access: Ensure that external connections are protected using secure networking and multi-factor authentication.
- Constant training: Instruct employees to identify phishing attempts and other common threats.
- Secure integration with Verifactu: Assess and secure all connections to external platforms to prevent data leaks or unauthorized access.
Cybersecurity as a key strategy
The Trinity case shows that data is a valuable asset, and protecting it must be a priority. The lesson is clear: It is not enough to rely on third-party systems , as any connected company can become the weak link in a vulnerable chain.
With Verifactu about to go live, the Cybersecurity no longer optional . Companies that manage data must adopt a preventive and strategic posture to protect their information, their reputation and the trust of their customers. In an environment where every connection is a potential gateway, data protection must be as consistent as billing itself.